ChatGPT Cybersecurity | Best 5 Prompts | Benefits and Risks
We are excited to share with you how ChatGPT is being used in the field of cybersecurity and the potential benefits and risks associated with its use. In this article, we'll explore various use cases of ChatGPT in cybersecurity, including threat intelligence, incident response, vulnerability management, security awareness training, and compliance. We'll also discuss the potential for malicious use of ChatGPT by attackers.
We will highlight some key benefits of integrating ChatGPT into cybersecurity operations, such as automating repetitive tasks, enhancing threat intelligence analysis, and improving incident response times. However, it's crucial to be aware of the potential risks and challenges, including data privacy and security concerns, the potential for misuse, hallucinations and inaccuracies, compliance and repetitional risks, and the danger of over-reliance and deskilling.
To help you effectively implement ChatGPT in your cybersecurity strategy, we will provide best practices and example prompts that you can use for various cybersecurity tasks. By the end of this article, you'll better understand how ChatGPT can be leveraged in cybersecurity and how to mitigate the associated risks.

Understanding ChatGPT in the Context of Cybersecurity
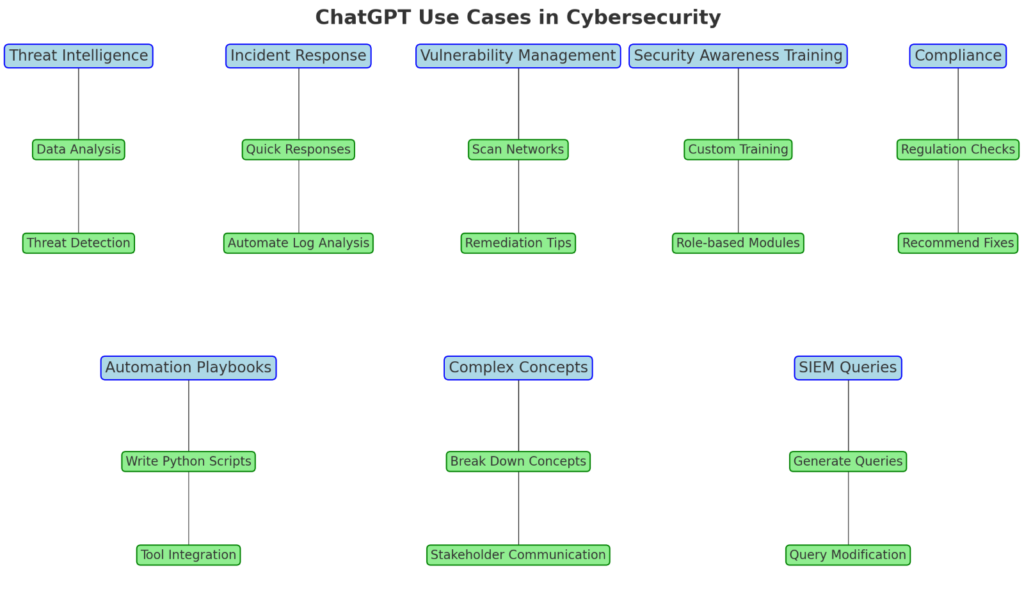
There are several examples of how ChatGPT is being used or could potentially be used in cybersecurity including:
| Use Cases | Description |
|---|---|
| Threat Intelligence | ChatGPT can help gather and analyze threat intelligence data from various sources to identify potential threats and vulnerabilities. |
| Incident Response | ChatGPT can be trained on previous incident reports to provide quick responses to similar incidents, helping reduce response time. It can also help automate repetitive tasks in Security Operations Centers (SOCs) like log analysis. |
| Vulnerability Management | ChatGPT can scan and identify vulnerabilities in an organization's network and provide remediation recommendations. |
| Security Awareness Training | ChatGPT can develop customized security awareness training programs for employees based on their roles. |
| Compliance | ChatGPT can help identify potential compliance issues with regulations like HIPAA and GDPR and provide remediation recommendations. |
| Generating SIEM Queries | Security analysts are using ChatGPT to quickly generate complex Splunk and other SIEM queries, which can then be modified as needed. |
| Developing Automation Playbooks | ChatGPT is being leveraged to assist with writing Python scripts for developing automation playbooks in tools like Splunk Phantom. |
| Explaining Complex Concepts | Analysts are asking ChatGPT to break down and explain relatively complex cybersecurity concepts in an understandable way, especially useful when communicating with non-technical stakeholders. |
| Analyzing SIEM Alerts | Microsoft has enabled plugins to use ChatGPT's API to send recommendations whenever a new incident is triggered in their Azure Sentinel SIEM. |
Benefits of Using ChatGPT in Cybersecurity
Integrating ChatGPT into cybersecurity operations can provide the following benefits:
Automation of repetitive tasks:
- ChatGPT can handle time-consuming tasks, like analyzing security logs and alerts, freeing up cybersecurity professionals to focus on more complex issues.
Enhanced threat intelligence analysis:
- Leveraging ChatGPT's natural language processing capabilities, cybersecurity teams can:
- Identify patterns and trends in threat data
- Gain valuable insights for proactive defense
Improved incident response times:
- ChatGPT can:
- Generate incident response playbooks
- Guide security teams through necessary steps
- Reduce response times and minimize the impact of security incidents

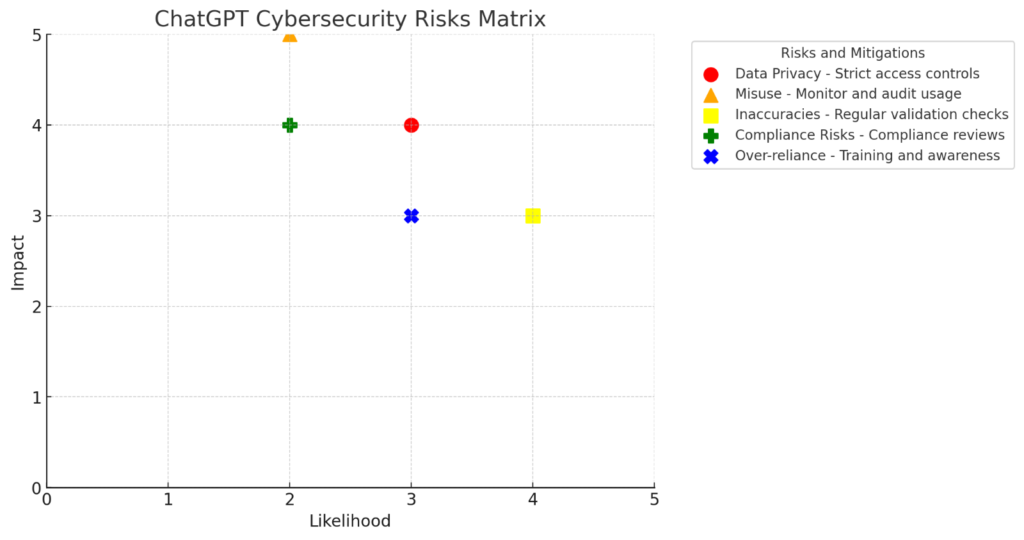
Potential ChatGPT Cybersecurity Risks and Challenges
Data privacy and security concerns
We need to be very cautious about entering confidential information, code, legal contracts, customer data, etc. into ChatGPT, as any sensitive data entered could potentially be exposed if there are data breaches or leaks at OpenAI. ChatGPT does not store data in a way that is sufficiently secure for handling sensitive information, and its data privacy measures may not meet the strict requirements of regulated industries.
ChatGPT has suffered a data breach in early 2023, exposing some users' personal information.
Potential for misuse
ChatGPT could be exploited by attackers to generate targeted phishing emails, malware code, and social engineering content, making cyber-attacks more sophisticated. Just as ChatGPT can be used by defenders, it can empower attackers to generate malware, discover vulnerabilities, and craft more persuasive social engineering lures, potentially spurring an AI-powered arms race.
Hallucinations, inaccuracies, and lack of explainability
ChatGPT can sometimes generate incorrect or nonsensical information ("hallucinations"). Relying on its outputs without human validation, especially for critical security functions, could lead to errors and vulnerabilities. The black-box nature of large language models like ChatGPT makes it difficult to understand its reasoning, which is critical for cybersecurity use cases.
Compliance and repetitional risks
Use of ChatGPT could violate data privacy regulations like HIPAA, GDPR, etc., if personal data is entered, which is a major concern in regulated industries. Any data leaks or misuse associated with ChatGPT could lead to repetitional damage for organizations.
Over-reliance and deskilling
If our security teams overrely on ChatGPT without developing expertise, this could lead to deskilling and overreliance on AI. Human judgment remains critical.
How to use ChatGPT for Cybersecurity?
To effectively integrate ChatGPT into your cybersecurity strategy, consider the following best practices:
- Collaborate with AI experts: Work closely with AI professionals to ensure the proper design, training, and deployment of ChatGPT models for cybersecurity purposes.
- Test and monitor: Continuously test and monitor ChatGPT's performance to identify and address any issues or inaccuracies promptly.
- Provide clear context and objectives: When creating ChatGPT prompts for cybersecurity tasks, provide clear context and specific objectives to guide the model's outputs.
- Consider legal and ethical aspects: Ensure that the use of ChatGPT complies with relevant laws, regulations, and ethical guidelines, particularly in handling sensitive data and making decisions that may impact individuals or organizations.
Example ChatGPT Cybersecurity prompts
Here are some example prompts that can be used to use ChatGPT for various cybersecurity tasks:
| Prompt Title | Prompt Description |
|---|---|
| Incident Response Plan | Act as a cybersecurity consultant. I need help developing an incident response plan for my organization, a mid-sized manufacturing company with 750 employees. The plan should cover preparation, detection, containment, eradication, recovery, and lessons learned. Provide an outline of the key components to include. |
| Cloud Security Architecture | Pretend you are an expert in cloud security architecture. My startup is building our product on Google Cloud Platform and we need guidance on implementing security best practices as we scale. Cover topics like IAM roles, encryption at rest and in transit, VPC networking, logging and monitoring, and secure CI/CD pipelines. Explain the concepts suitable for a non-technical founder. |
| Security Awareness Training | I am a CISO at a large financial institution. Generate ideas for an engaging and effective security awareness training program to educate our employees and contractors on topics like business email compromise, insider threats, secure remote work, and incident reporting. The program should include a variety of content formats and reinforce learning throughout the year. |
| Malware Analysis | Act as a malware analyst. I am investigating a potential ransomware attack and have obtained a suspicious email attachment. Walk me through the steps to safely analyze the malware in an isolated environment, reverse engineer it to understand its capabilities, and develop IoCs to detect other infected systems. Assume I have basic skills with tools like Ghidra and Wireshark. |
| Privacy by Design | I want you to be a privacy expert. My organization is implementing a privacy by design framework for our new mobile app to comply with GDPR, CPRA, and other data protection regulations. Provide guidance on key principles to follow, how to conduct privacy impact assessments, and best practices for data minimization, retention, and security. Use plain language suitable for a general audience. |





